Introduction
Ensuring data protection and privacy has become an urgency in today’s digitalized world. Data breaches have heightened noticeable awareness around data protection and privacy [1]. The supply of different digital services and applications that are tapping into the value of the unlimited resource of personal data is constantly increasing. The development of digital technology has not only shaken the debate about an individual’s right to privacy but has also forced progress within the legal regulatory framework. Privacy is yet to be a top priority within companies, as privacy is often assured solely by compliance with regulatory frameworks. However, it can become very expensive and burdensome to rectify privacy concerns in retrospect and a possible privacy invasive event may already have damaged customer trust and loyalty beyond repair and may have caused financial and reputational losses, lawsuits and even claims for damages. Privacy by Design is the approach to battle these concerns by engineering privacy into products and services.
The fundamental goal of Privacy by Design is to design privacy-compliant products and services by addressing privacy concerns already in the development phase. This document discusses, how to implement Privacy by Design through privacy engineering.
Privacy by Design
Although Privacy by Design dates back to 1990’s, it is still somewhat of an abstract concept. For example, Privacy by Design consists of a number of principles that can be applied from the onset of development to mitigate privacy concerns and achieve data protection compliance. However, these principles remain vague and leave many open questions about their application when engineering systems [2]. It is a substantial challenge for organizations today to find a way to do this, i.e. the concrete means to implement privacy-enhancing features in deliverables. After the introduction of General Data Protection Regulation (GDPR) [3], Privacy by Design got included in regulatory requirements further emphasizing the importance of it; it is only a matter of time until the first legal interpretations of Privacy by Design will be available.
Privacy Engineering
Privacy engineering is usually referred as the implementation process to achieve Privacy by Design. If Privacy by Design explains “What” to do, privacy engineering explains “How” to do it. In a business context, privacy engineering starts from company’s privacy principles defining high-level objectives to process personal data. These principles are implemented or engineered through various activities. These activities can be implemented as organizational controls and technical controls to achieve Privacy by Design (see Figure 1.)
Figure 1. Privacy principles are converted to implementation through organizational and technical controls.
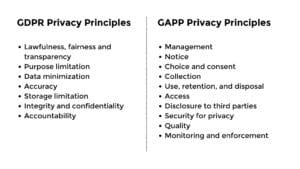
The core of Privacy by Design is a set of internationally recognized foundational principles [4] that can be applied throughout the development process of deliverables, from onset to launch, in order to mitigate privacy concerns and achieve data protection compliance. Commonly, privacy principles are derived directly from regulation or industry best practices. Examples of such principles are GDPR privacy principles and GAPP privacy principles (see Figure 2.).
Any chosen principles are useful to create a structure for privacy engineering and they are commonly used in e.g. executive reporting to hide excessive details and complexity. Privacy principles are converted to implementation through organizational and technical controls.
ORGANIZATIONAL CONTROLS
Organizational controls are a set of activities that are setting process controls to ensure the implementation of privacy. These controls do not necessarily affect the implementation but are crucial in creating transparency and accountability in an organization. Examples of recognized organizational controls are:
- Data Inventory and Classification
Ideally, all customer data collection should be planned before any data is collected and registered continuously as the data is processed. However, if this is not the case, a data inventory must be conducted as a first step in order to identify, understand and document all relevant data processes. A data inventory and classification process means a continuous review and documentation of all the collected pieces of data in the possession of a company. Through a data classification process, personal data is categorized and assigned a certain sensitivity level, which is needed in order to determine the correct risk profile.
- Privacy Risk Management
Within the field of data protection and privacy, risks are usually perceived as consequences due to non-compliance with applicable legislation and policies, weaknesses within an existing system, threats to them or the possibility of privacy invasive events that would have a negative impact on the privacy of data subjects. As Privacy by Design strives to tackle privacy risks already at the drawing table, identifying the correct risk profile is therefore essential. A typical approach to implement privacy risk management is Privacy Impact Assessment, PIA (see Figure 3). PIA is a tool that helps a company identify privacy risks in any deliverables, or processes or prospective projects that process personal data
Figure 3. Privacy Impact Assessment (PIA) helps companies to identify privacy risks.
- Privacy Trainings
Privacy trainings intend to provide necessary privacy awareness amongst workforce. Majority of privacy breaches are being caused by a human error and raising awareness level is a powerful tool to avoid such issues.
Organizational controls are not limited to the above-mentioned examples. An organization, business models and other similar aspects are defining final controls necessary in a given organization.
TECHNICAL CONTROLS
The technical controls are affecting an implementation through creating controls or functionality to a product. In the best case, technical controls are resulting into adding something to software code, demonstrating privacy by design at the best possible level. Examples of technical controls are:
- Privacy Requirements
Applicable privacy requirements can be found in branch or industry specific business practices, various standards, laws and regulations. It is a typical approach to gather from relevant sources so called “minimum” or “baseline” requirements that must be followed in development process. Furthermore, such requirements can e.g. be used as a checklist to gain assurance on adequate implementation level of privacy.
- Design Patterns
Design pattern are general solutions to commonly occurring problems. Privacy design patterns are a way into practical advice to software development through documenting a solution using standardized terminology. It is a typical approach to standardize some solutions like “How to give a notice?” for unified user interface design.
- Privacy Enhancing Technologies
Privacy Enhancing Technologies (PETs) are technologies that are designed for supporting privacy and data protection. In the best case, PET can be applied “as is” in implementation to implement desired requirement or control. Examples of PETs are:
-
- Encryption Protocols: Use of standard cryptographic protocols like Transport Layer Security (TLS) to ensure confidentiality of personal data at transit.
- Cookie Consent Toolkit: Use of available toolkits for managing uses of cookies and to keep records, audit trail and demonstrate compliance with regulation.
- Anonymization Tools: Use available anonymization tools to remove personal data automatically from the source data to e.g. share data.
Technical controls are not limited to the above-mentioned examples. An organization, business models and other similar aspects are defining final controls necessary in a given organization.
Summary
Privacy by Design is the approach to integrate privacy into proactively to products and services throughout the lifecycle of a product or a service. The challenge with Privacy by Design is that it is considered to be too vague or high-level to be applied in engineering products and services. Privacy engineering is considered as the approach to implement Privacy by Design. Successful implementation of privacy engineering results into integration of organizational and technical controls to the development process. Privacy engineering must never be a separate process to the development process; it must be integral part of the product development process to ensure successful implementation of Privacy by Design.
Help with Privacy Engineering?
Privaon can help to implement Privacy by Design in products and services. This is done by creating a customized privacy engineering process, integrate it to customers development process, and make training material to educate engineers to follow the process.
We have developed several privacy engineering processes for our customers. If you are interested to hear more, please do not hesitate to contact us.